Last week I wrote about forwarding Aria Operations alerts with SNMPv3. Since Ubuntu is widely used I have decided to test also Ubuntu in my lab.
In this blog post I will describe the steps taken to send an SNMPv3 trap from Aria Operations to Ubuntu where the traps are stored readably in a log file. For this test, I used the following configuration:
- VMware vCenter 8.0 update 2a
- VMware ESXi 8.0 update 2
- VMware Aria Operations version: 8.14.1
- Linux Ubuntu 22.04.3 LTS
- NET-SNMP 5.9.1
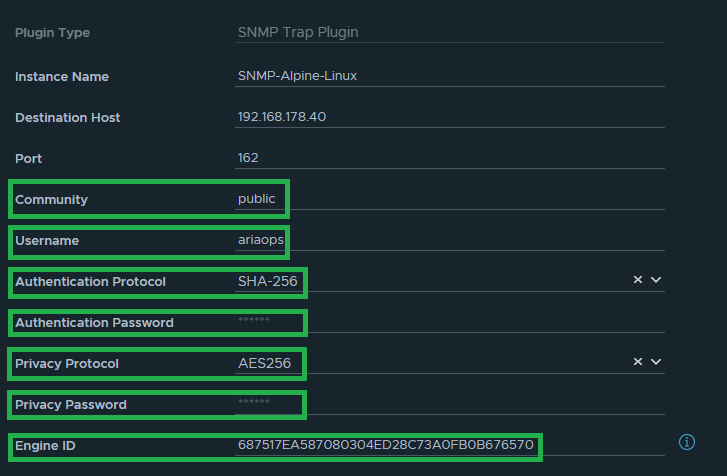
First step: Configure Aria Operations SNMP Trap Instance (Configure > Alerts > Outbound Settings > Add)
The name of the SNMP instance in my lab is “SNMP-UBUNTU”
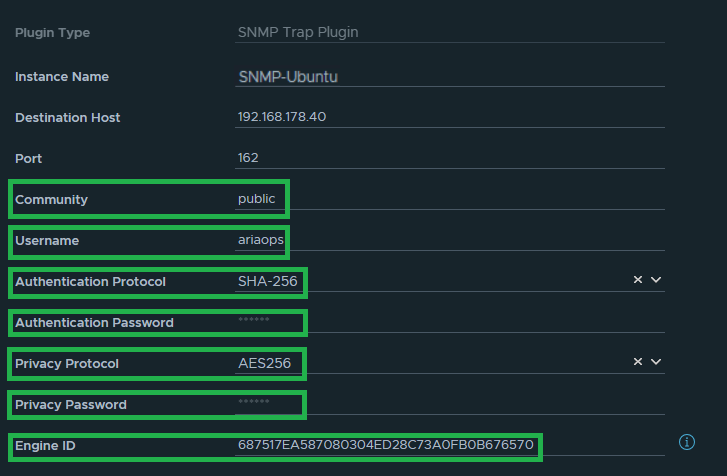
The data highlighted in green later is needed later when configuring the Linux SMMP trap collector. For both the Authentication Password and Privacy Password, we use the same password, which is “T3st123!”.
Second step: Install and configure the Linux SNMP trap collector.
Install Ubuntu 22.04
Once Ubuntu is installed, snmptrapd need to be installed. Note that from version NET-SNMP 5.9.x onwards, AES256 can be used, which is needed to decode SNMPv3 traps.
Install snmptrapd
apt-get update apt-get -y install snmptrapd apt update apt -y install snmptrapd
Create /var/log/snmptrapd.log
touch /var/log/snmptrapd.log chmod 666 /var/log/snmptrapd.log
Modify /usr/lib/systemd/system/snmptrapd.service to write traps to /var/log/snmptrapd.log
#Modify snmptrapd.service #Comment out the next line #ExecStart=/usr/sbin/snmptrapd -LOw -f udp:162 udp6:162 #Add the next line ExecStart=/usr/sbin/snmptrapd -LOw -f udp:162 udp6:162 -Lf /var/log/snmptrapd.log
Modify /etc/snmp/snmptrapd.conf
#Add the next lines disableAuthorization yes authCommunity log,execute,net public createUser -e 687570118567EE5F48839F4D0C2B8AE5312C ariaops SHA-256 T3st123!! AES-256 T3st123!! authUser log,execute,net ariaops format2 %.4y-%.2m-%.2l %.2h:%.2j:%.2k %B [%b]:\n%v\n outputOption s
Reload snmptrapd
systemctl daemon-reload systemctl restart snmptrapd.service
Add Ubuntu MIB files
apt-get install snmp-mibs-downloader
Download the Aria Operations MIB files from the Aria Operations appliance. See VMware KB2118780. This is needed to convert the Aria Operations in readable alerts in the snmptrapd.log. See the next two Aria Operations test traps why the Aria Operations MIB files are needed.
First screenshot, the Aria Operations MIB files are not imported in Ubuntu. It cannot be seen that these alerts are VMware alerts
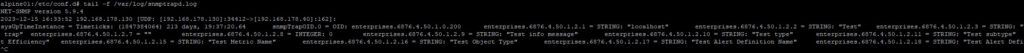
Next screenshot, the Aria Operations MIB files are imported in Ubunti. Now it is clear that these are VMware events.
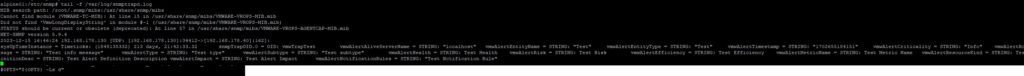
#Download the Aria Operations MIB files from this directory /usr/lib/vmware-vcops/user/plugins/outbound/vcops-snmptrap-plugin/mib
Upload the Aria Operations MIB files from the Aria Operations appliance to Ubuntu
#Upload the Aria Operations MIB files into this directory /usr/share/snmp/mibs
Modify /etc/snmp/snmp.conf
#Comment out mibs #mibs : #Add custom Aria Operations MIB files mibs +VMWARE-ROOT-MIB mibs +VMWARE-VROPS-AGENTCAP-MIB mibs +VMWARE-VROPS-MIB mibs +VMWARE-PRODUCTS-MIB
Restart snmpd and snmptrapd
systemctl restart snmpd.service systemctl restart snmptrapd.service
Third step: Test if Aria Operations SNMPv3 traps are received on the Linux SNMP collector
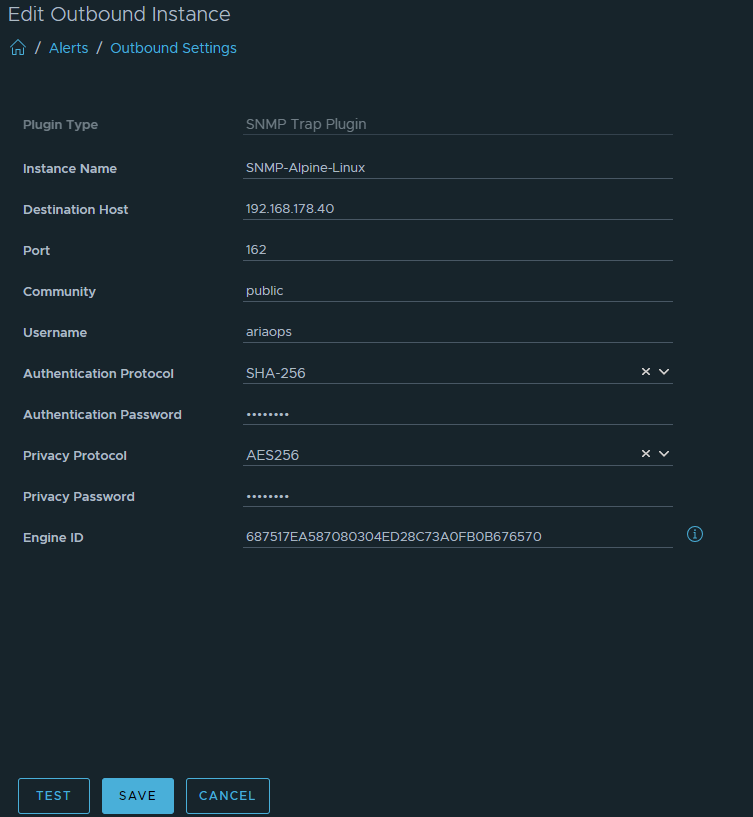
Test 1: Sending a test trap from the Aria Operations SNMP instance.
Note that before testing both password have been entered. Otherwise the test will fail.
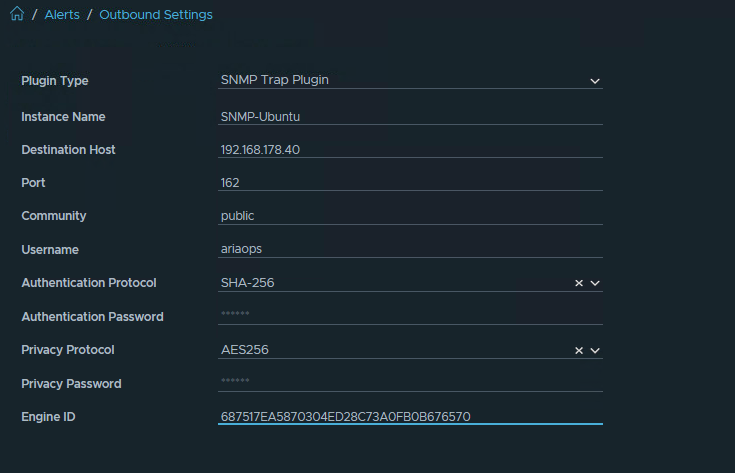
Hit the “TEST” button. The following message will appear.
Check the snmptrapd.log (tail -f /var/log/snmptrapd.log) and search for “Test Notification Rule”
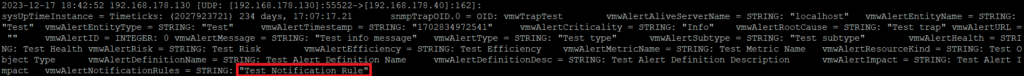
We see “Test Notification Rule” in the snmptrad.log. Test is succeeded.
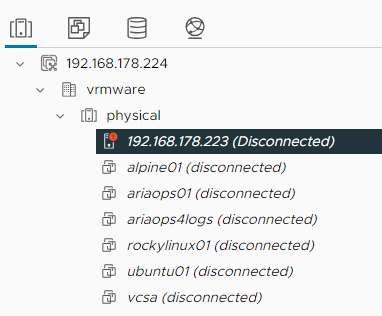
Test2: Disconnect a ESXi host from vCenter
I have created a notification that wil send a SNMP trap to the LinuxSNMP collector.
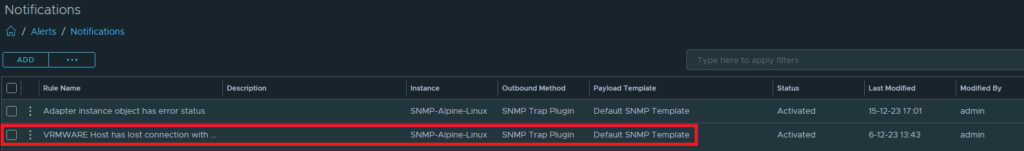
Disconnect ESXi host from vCenter:
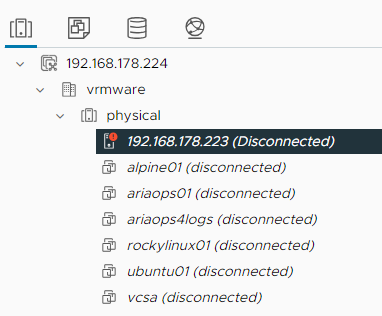
Alert is raised in Aria Operations
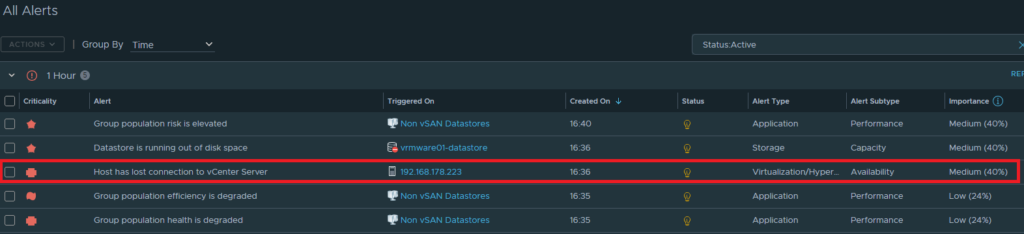
Check the snmptrapd.log (tail -f /var/log/snmptrapd.log) and search for “Host disconnected from vCenter”
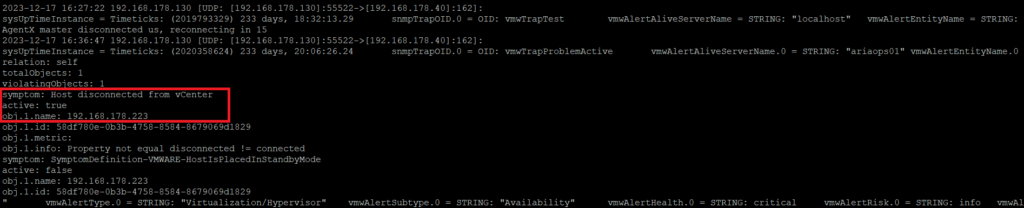
We see “Host disconnected from vCenter” in the snmptrad.log. Test is succeeded.
From here, the alerts can move on to the third-party monitoring tool. That is beyond the scope of this test. Hopefully this blog post is useful to you.