Recently a question came up whether it is possible to forward Aria Operations alerts to a third-party monitoring tool using SNMPv3. I had no experience with this until that point. During this exploration it turns out that there is a lot of information to be found about configuring a SNMPv3 target. It turned out to be quite a search to find the right information to be able to decode the SNMPv3 traps and write them readable away in a log file. I tested with several types of Linux, including Raspberry Pi and Rocky Linux 9, but in the end I succeeded with Alpine Linux. An added advantage of Alpine is that it is lightweight.
In this blog post I will describe the steps taken to send an SNMPv3 trap from Aria Operations to a Linux collector where the traps are stored readably in a log file. For the test, I used the following configuration:
- VMware vCenter 8.0 update 2a
- VMware ESXi 8.0 update 2
- VMware Aria Operations version: 8.14.1
- Linux Alpine Standard 3.19.0 x86_64
- NET-SNMP 5.9.4
First step: Configure Aria Operations SNMP Trap Instance (Configure > Alerts > Outbound Settings > Add)
The name of the SNMP instance in my lab is “SNMP-Alpine-Linux”
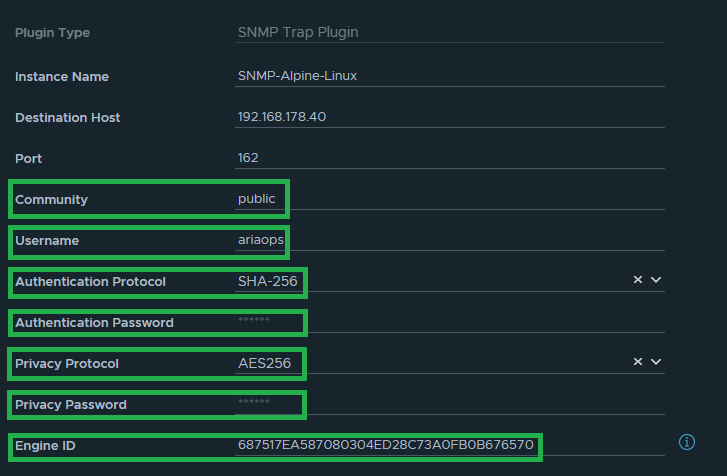
The data highlighted in green later is needed later when configuring the Linux SMMP trap collector. For both the Authentication Password and Privacy Password, we use the same password, which is “T3st123!”.
Second step: Install and configure the Linux SNMP trap collector.
Install Alpine Linux. Click here for the Alpine Wiki.
Once Alpine is installed, NET-SNMP can be installed. Note that from version NET-SNMP 5.9.x onwards, AES256 can be used, which is needed to decode SNMPv3 traps.
Install NET-SNMP
apk update && apk add net-snmp net-snmp-tools
Modify /etc/snmp/snmp.conf
In this step we will need the green marked higlighted data from the Aria Operations SNMP instance.
####################################################################### # Example configuration file for snmptrapd # # No traps are handled by default, you must edit this file! # # authCommunity log,execute,net public # traphandle SNMPv2-MIB::coldStart /usr/bin/bin/my_great_script cold ######################################################################## authCommunity log,execute,net public #AriaOps #createUser -e <ENGINE-ID> <USERNAME> <AUTHENTICATION PROTOCOL> <AUTHENTICATION PASSWORD> <PRIVACY PROTOCOL> <PRIVACY PASSWORD> createUser -e 687517EA587080304ED28C73A0FB0B676570 ariaops SHA-256 T3st123! AES-256 T3st123! ###################################### authUser log,execute,net ariaops format2 %.4y-%.2m-%.2l %.2h:%.2j:%.2k %B [%b]:\n%v\n outputOption s
Modify /etc/conf.d/snmptrapd
Here we unmark #OPTS=”${OPTS} -Lf /var/log/snmptrapd.log” so snmp traps will be logged in /var/log/snmptrapd.log.
# extra flags to pass to snmptrapd
OPTS=""
# ignore authentication failure traps
#OPTS="${OPTS} -a"
# log messages to specified file
OPTS="${OPTS} -Lf /var/log/snmptrapd.log"
# log messages to syslog with the specified facility
# where facility is: 'd' = LOG_DAEMON, 'u' = LOG_USER, [0-7] = LOG_LOCAL[0-7]
#OPTS="${OPTS} -Ls d"
Restart snmptrapd
/etc/init.d/snmptrapd restart of systemctl restart snmptrapd
Create snmptrapd.log
touch /var/log/snmptrapd.log
Download the Aria Operations MIB files from the Aria Operations appliance. See VMware KB2118780. This is needed to convert the Aria Operations in readable alerts in the snmptrapd.log. See the next two Aria Operations test traps why the Aria Operations MIB files are needed.
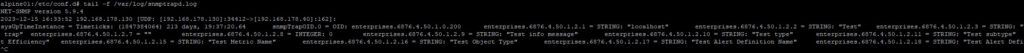
First screenshot, the Aria Operations MIB files are not imported in Alpine. It cannot be seen that these alerts are VMware alerts
Next screenshot, the Aria Operations MIB files are imported in Alpine. Now it is clear that these are VMware events.
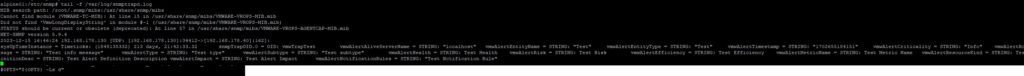
#Download the Aria Operations MIB files from this directory /usr/lib/vmware-vcops/user/plugins/outbound/vcops-snmptrap-plugin/mib
Upload the Aria Operations MIB files from the Aria Operations appliance to Alpine
#Upload the Aria Operations MIB files into this directory /usr/share/snmp/mibs
Create /etc/snmp/snmp.conf
touch /etc/snmp/snmp.conf
Add the custom Aria Operations MIB files to snmp.conf
#Add custom Aria Operations MIB files mibs +VMWARE-ROOT-MIB mibs +VMWARE-VROPS-AGENTCAP-MIB mibs +VMWARE-VROPS-MIB mibs +VMWARE-PRODUCTS-MIB
Restart snmpd and snmptrapd
/etc/init.d/snmpd restart /etc/init.d/snmptrapd restart
Auto start snmpd and snmptrapd at boot
rc-update add snmpd default rc-update add snmptrap default
Third step: Test if Aria Operations SNMPv3 traps are received on the Linux SNMP collector
Test 1: Sending a test trap from the Aria Operations SNMP instance.
Note that before testing both password have been entered. Otherwise the test will fail.
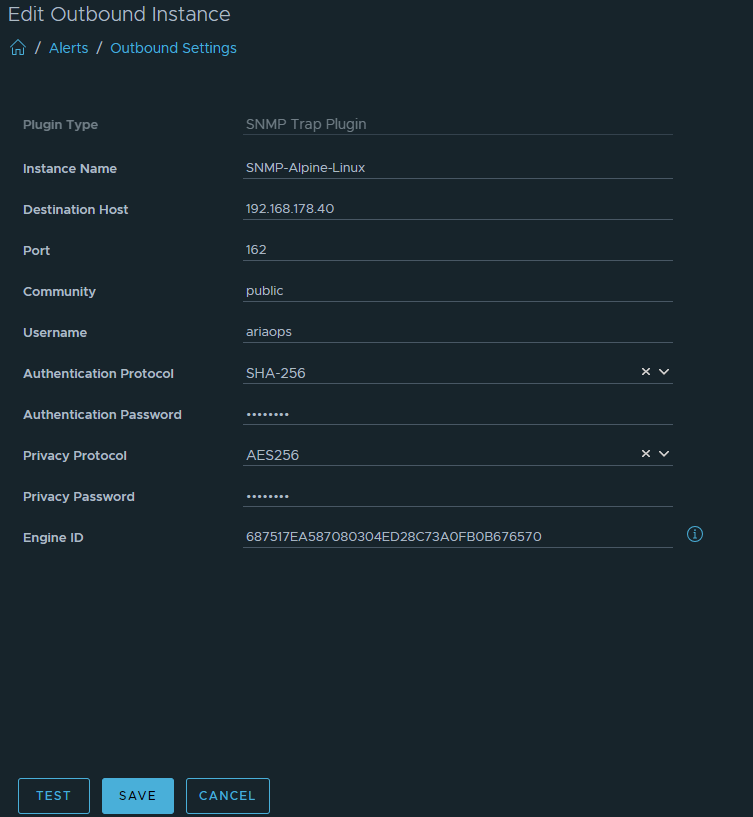
Hit the “TEST” button. The following message will appear.
Check the snmptrapd.log (tail -f /var/log/snmptrapd.log) and search for “Test Notification Rule”
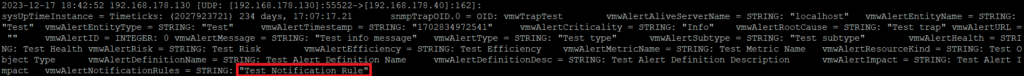
We see “Test Notification Rule” in the snmptrad.log. Test is succeeded.
Test2: Disconnect a ESXi host from vCenter
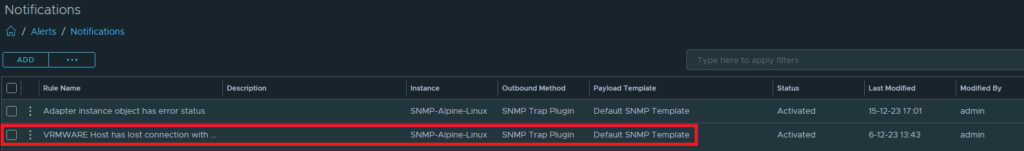
I have created a notification that wil send a SNMP trap to the LinuxSNMP collector.
Disconnect ESXi host from vCenter:
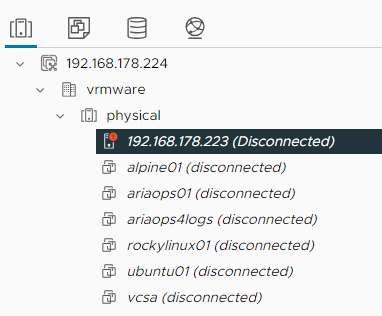
Alert is raised in Aria Operations
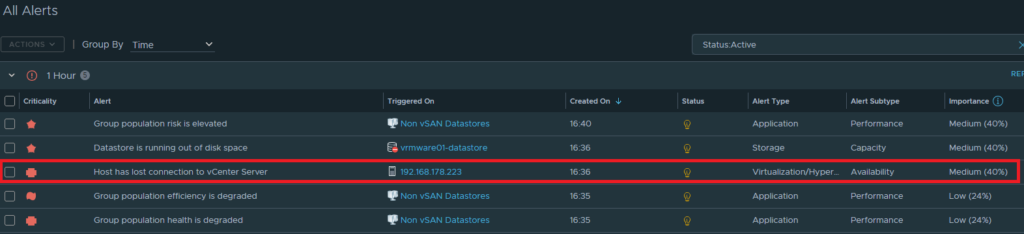
Check the snmptrapd.log (tail -f /var/log/snmptrapd.log) and search for “Host disconnected from vCenter”
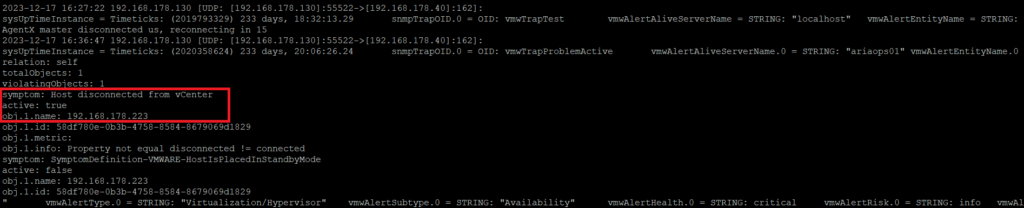
We see “Host disconnected from vCenter” in the snmptrad.log. Test is succeeded.
From here, the alerts can move on to the third-party monitoring tool. That is beyond the scope of this test. Hopefully this blog post is useful to you.

