This blog is the follow-up to the one I wrote earlier this week about sending VMware Aria Operations for Logs alerts to Microsoft (MS) Teams. This article describes the steps to forward alerts from VMware Aria Operations (Aria Ops) to MS Teams.

Use Case – Increase the ability to notice prio 1 alerts outside of office hours with the available technical resources.
Goal – In addition to the standard Aria Ops alerts, we also want to have the option available to receive alerts through Microsoft Teams.
Solution – Use Aria Ops Webhook to send alerts to MS Teams
Setup – In order to have Aria Ops alerts sent to MS Teams, we need to set up two things.
- Setup a MS Teams Connector to receive alerts
- Setup the Aria Ops Webhook configuration to push alerts
Setup a MS Teams Connector to receive alerts
First, decide in which Teams Channel you want to receive the Aria Ops alerts or add a new Teams Channel. I have created a new Channel called VRMware VMware Alerts.

Click on the 3 dots on the right side and select Manage Channel.
Select Edit under Connectors.
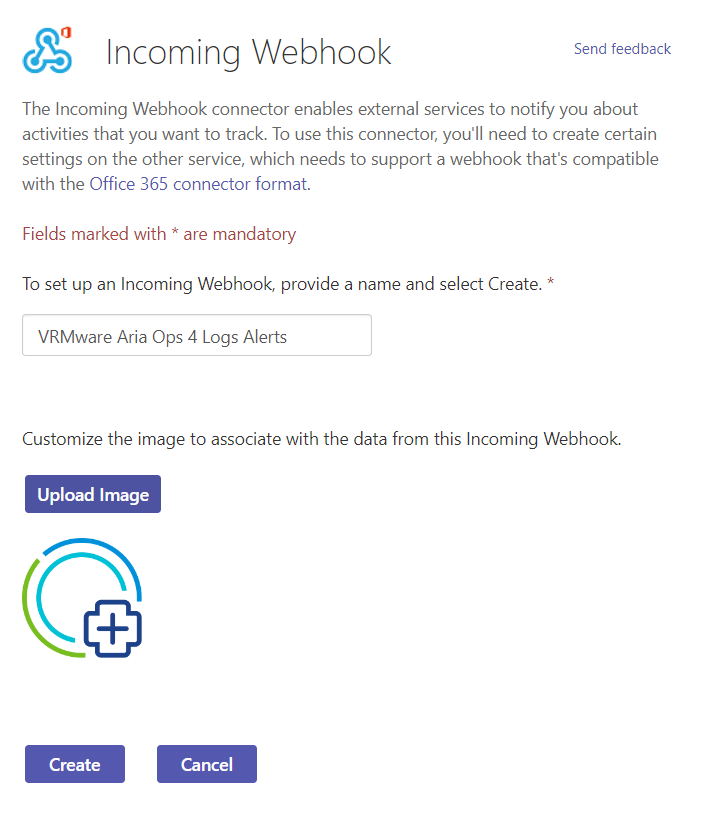
Select Incoming Webhook and hit the Configure button.
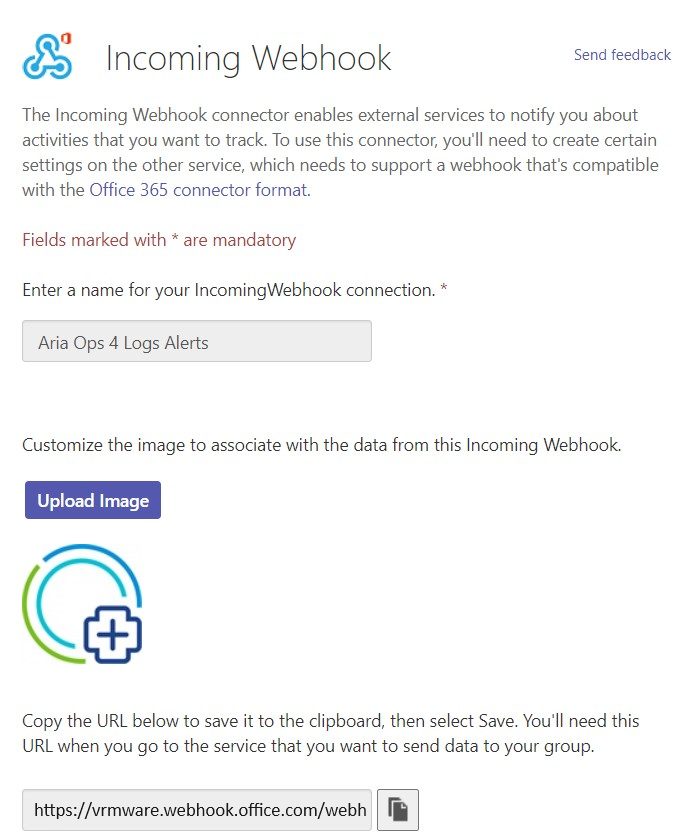
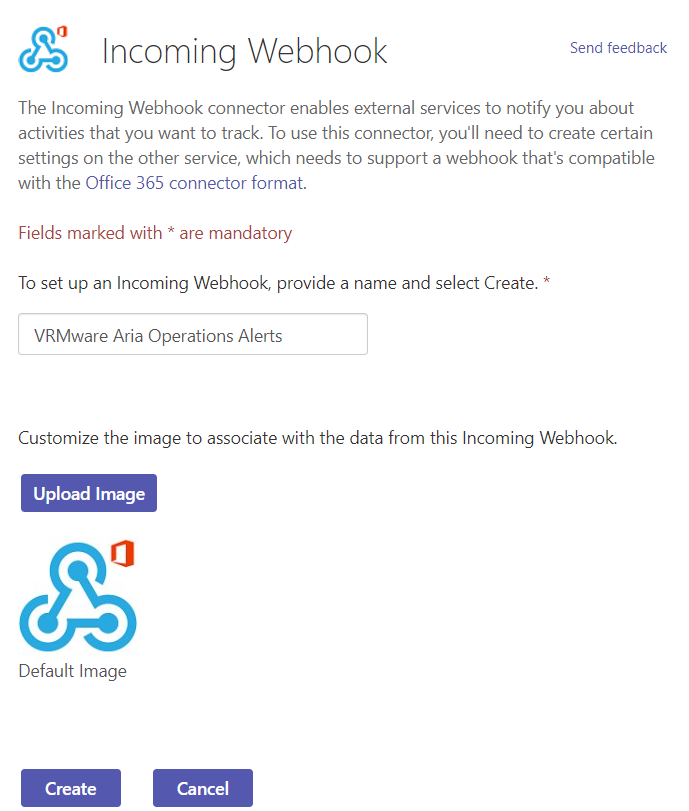
Provide a friendly name, upload an image and create the connector.
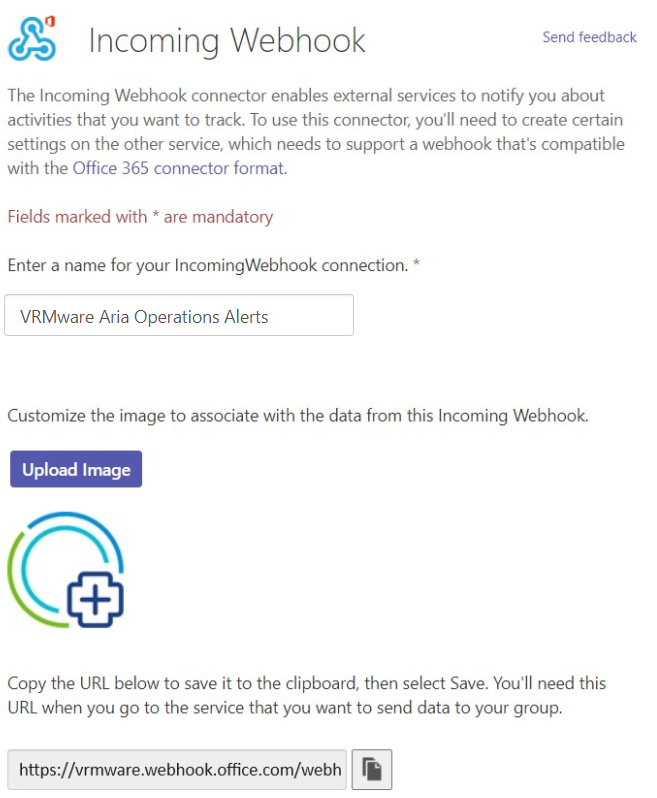
After creation copy the url to the clipboard. We need this URL later to configure the AO4L Webhook.
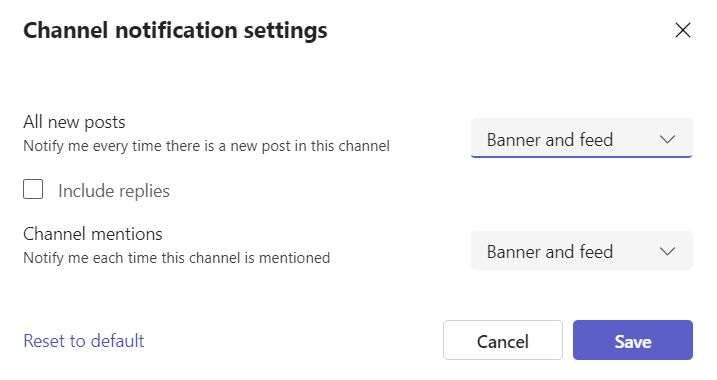
Before we move on to Aria Ops we need to enable the channel notifications. Click once again on the 3 dots on the right side and select Channel notifications > All New Posts.
Setting up Aria Ops Webhook configuration to push alerts
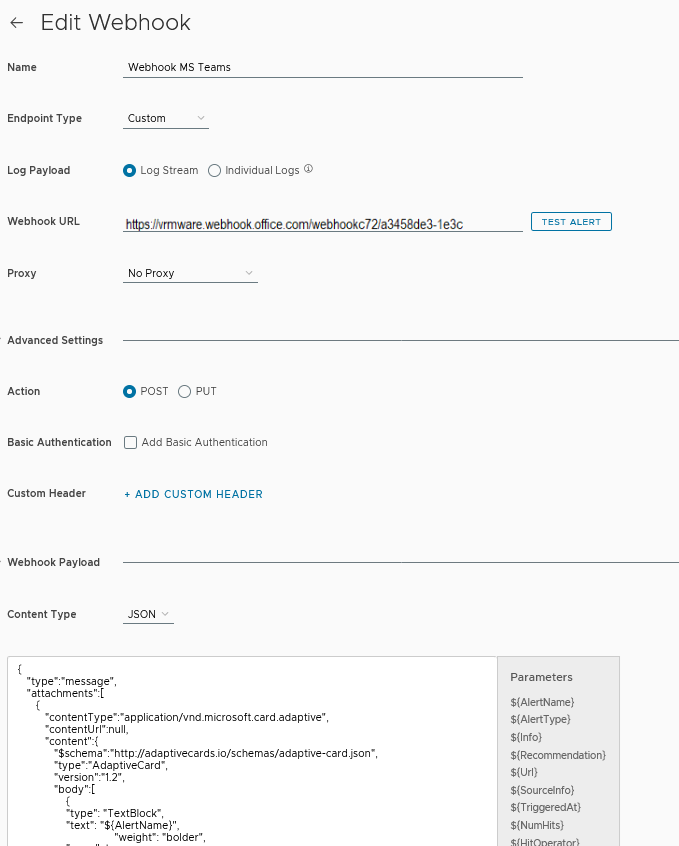
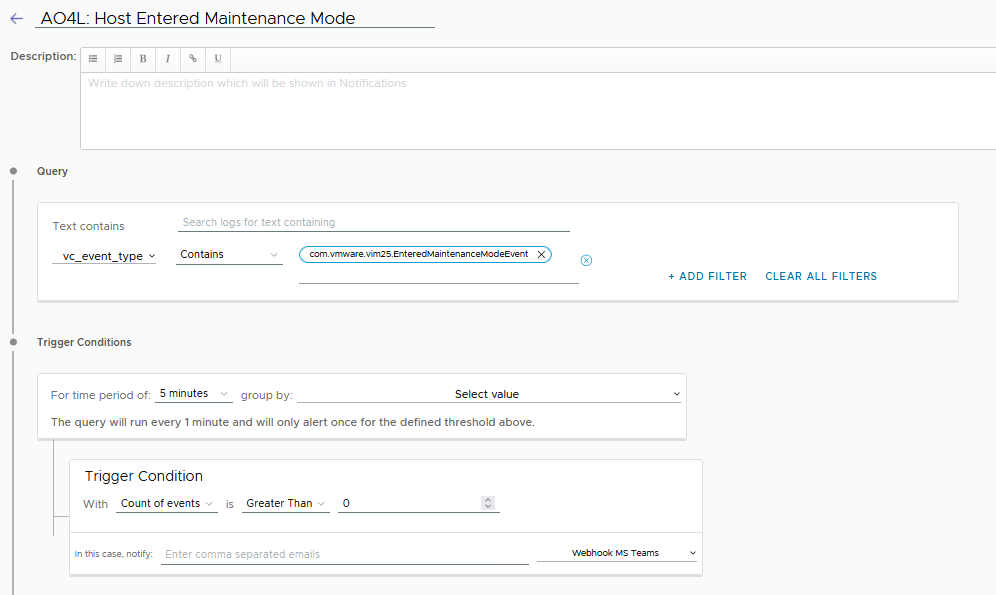
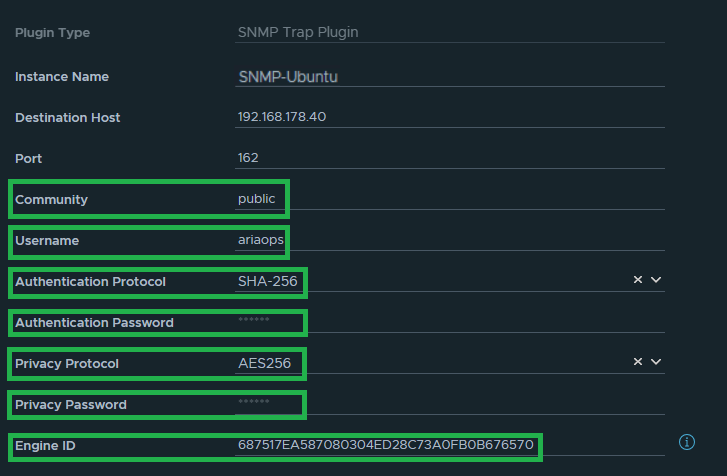
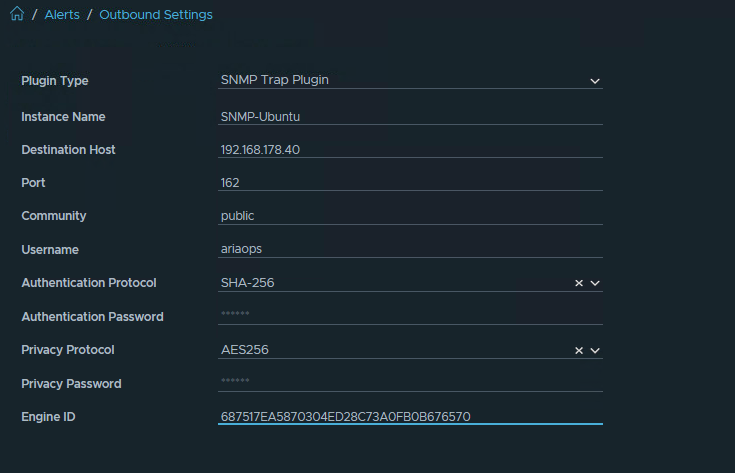
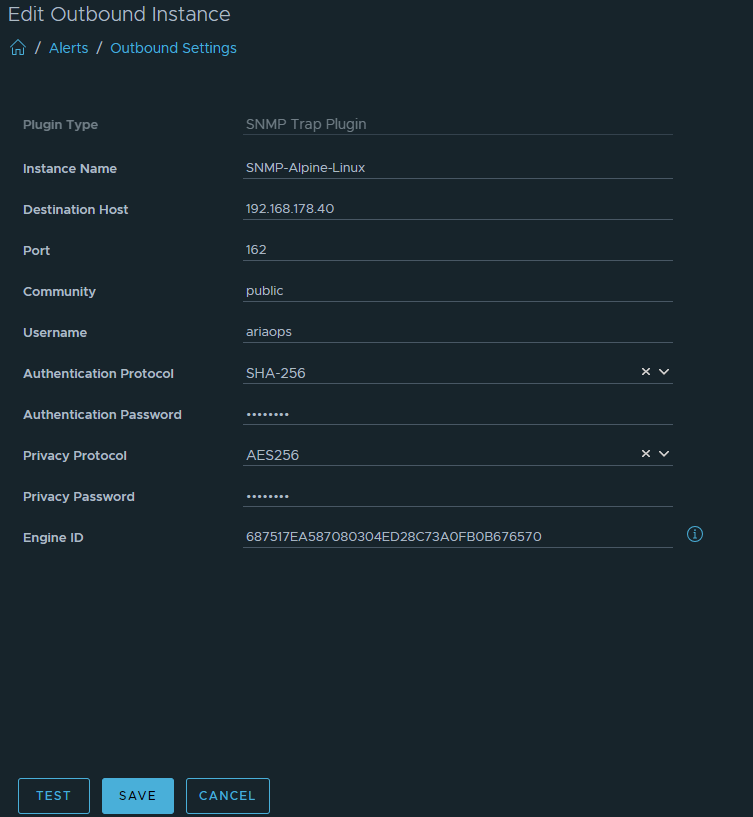
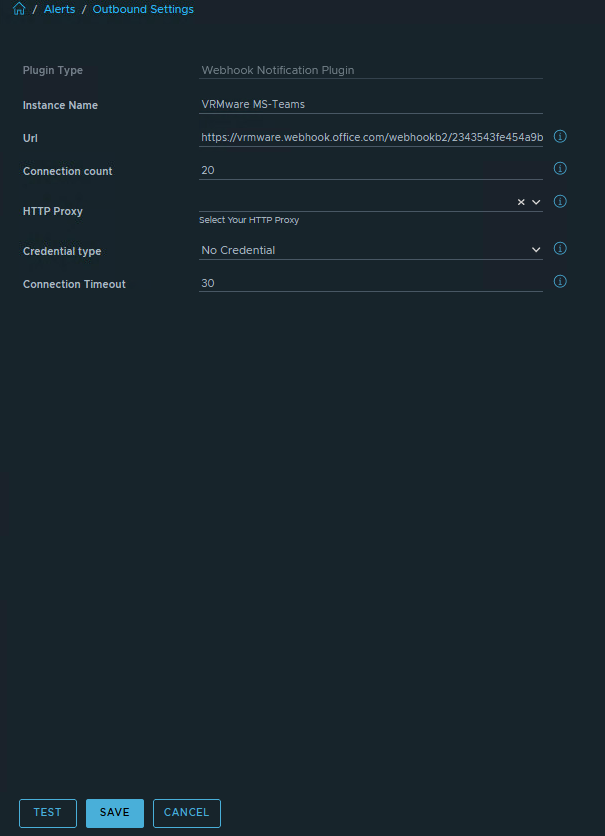
Go to Configure > Alerts > open Outbound Settings > Add > Plugin Type > Webhook Notification Plugin. Choose a Instance name. Copy the Webhook URL that was copied from MS Teams connector. Save, Test option does not work.
Webload Payload
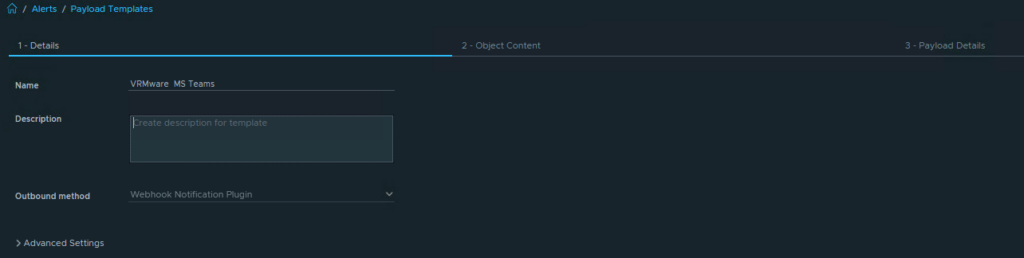
Go to Configure > Alerts > Payload Templates > Add > Create Payload Template > Details. Choose a frienly name and select the Outbound Method.
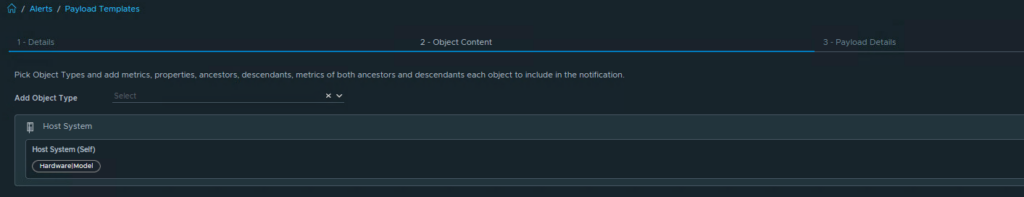
On the next tab, Object Content we select Host System and Hardware|Model as property. This is just an example. Choose what you like to monitor.
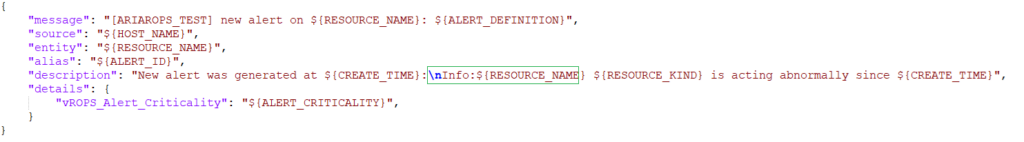
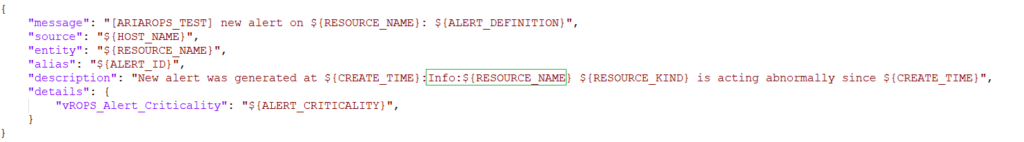
On the next tab, Payload Details we add the Payload code.
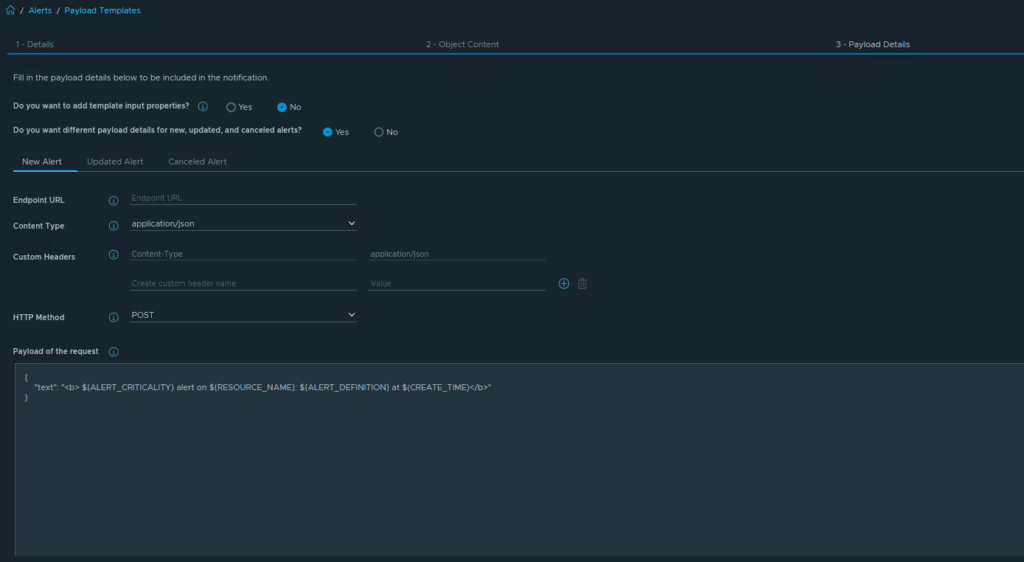
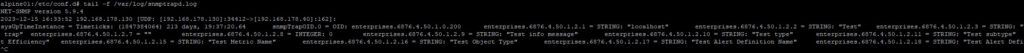
The Payload code that is used in the Payload Details tab.
{
"text": "<b> ${ALERT_CRITICALITY} alert on ${RESOURCE_NAME}: ${ALERT_DEFINITION} at $(CREATE_TIME)</b>"
}
After completing the Webhook configuration we want test the Webhook configuration.
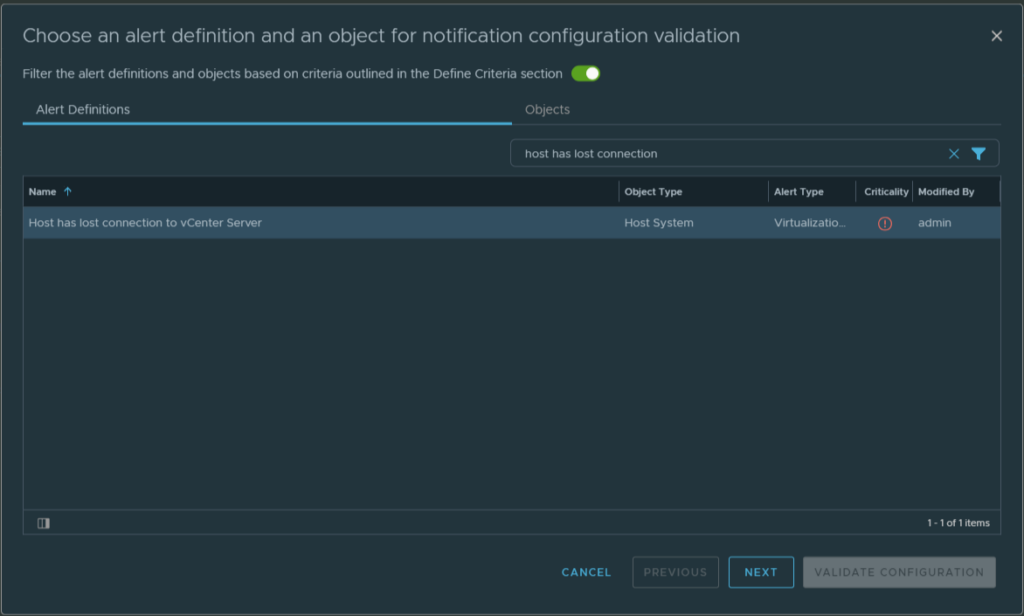
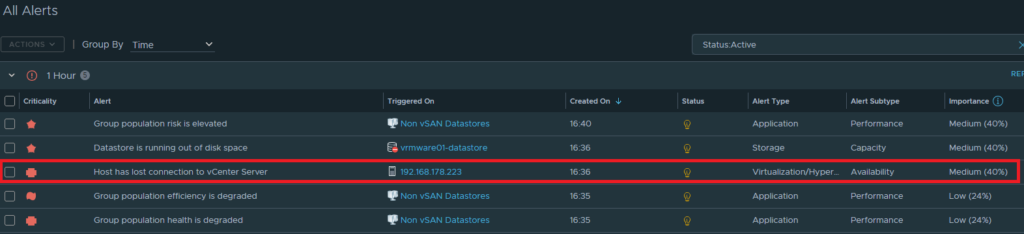
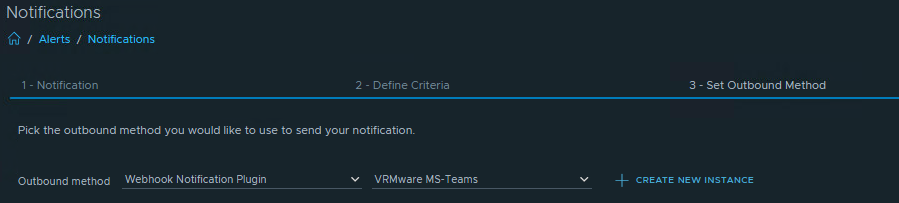
Create an alert, in our test case we use alert “Host has lost connection to vCenter Server“. Then we select the Outbound method “Webhook Notifcation Plugin” “VRMware MS-Teams“.
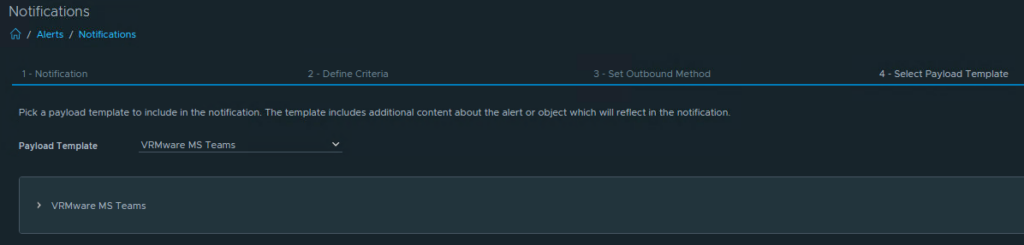
Next step is select the Payload Template.
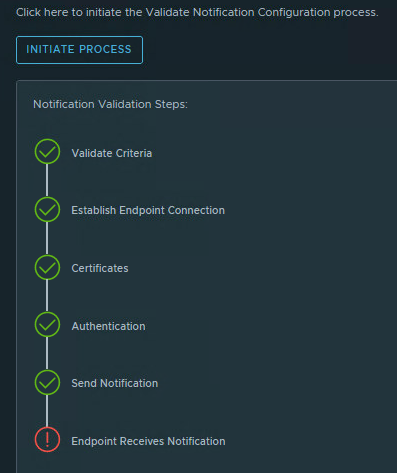
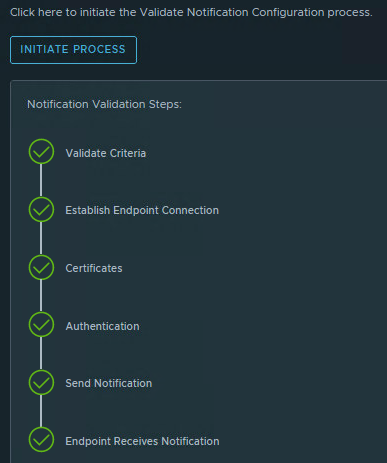
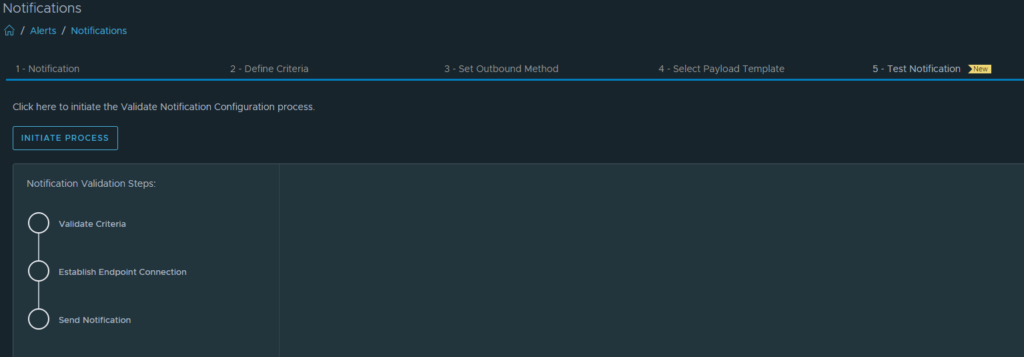
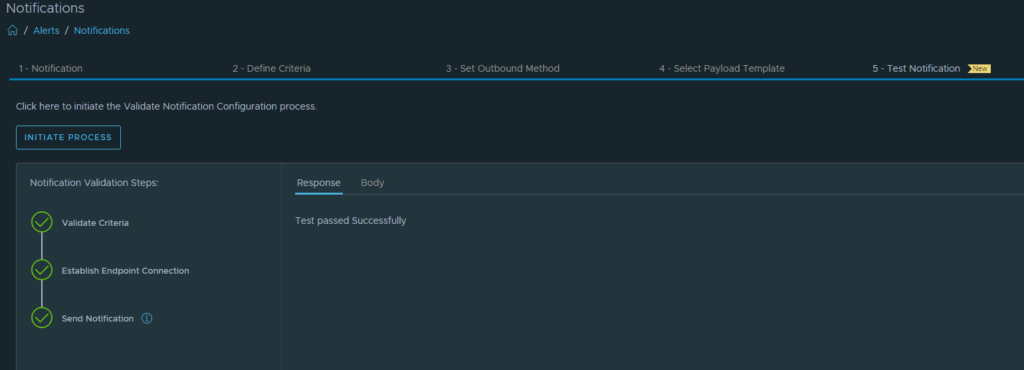
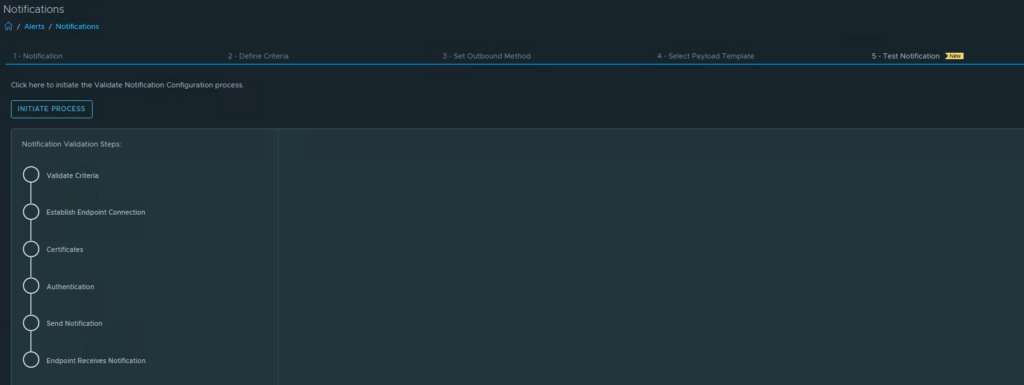
Finally, we are almost there to send a test alert. We do this on the Test Notifcation tab. Hit the “Initiate Process” button.
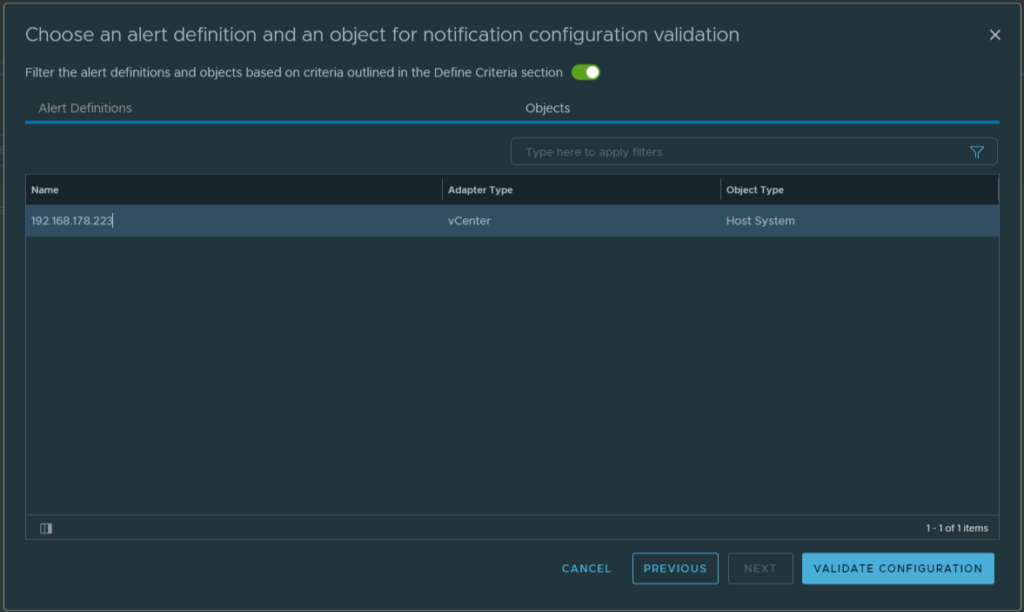
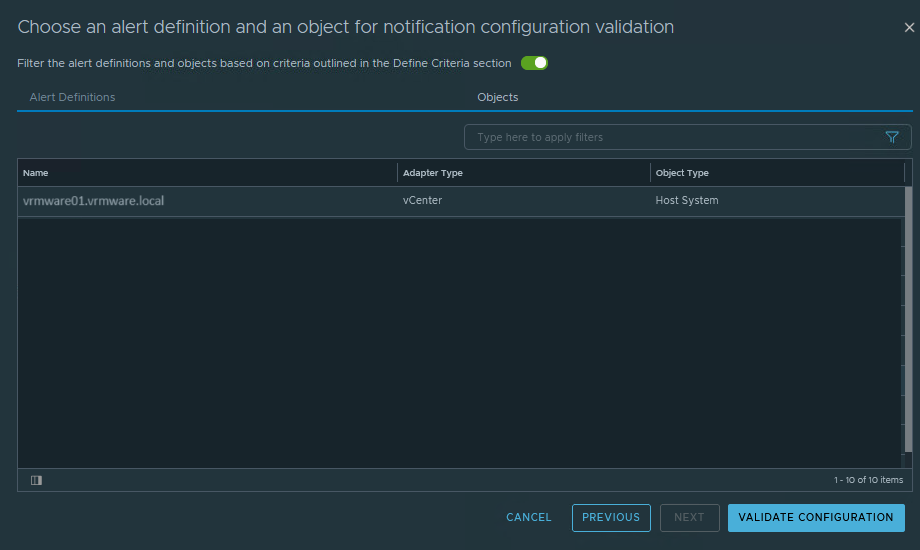
We select the Alert Definitions “Host has lost connection to vCenter Server“. We also use the filter the alert definition… option.
Select a host and validate the configuration.
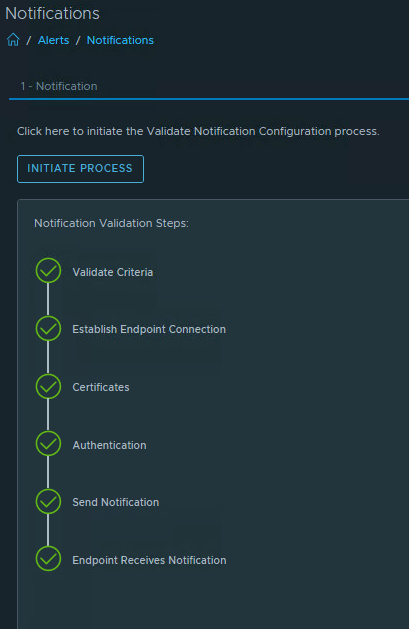
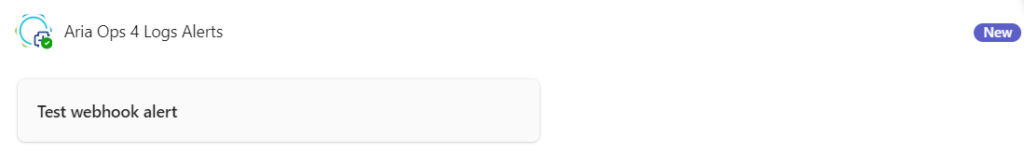
Now we can close the alert in Aira Ops. In Teams we have received the alert.
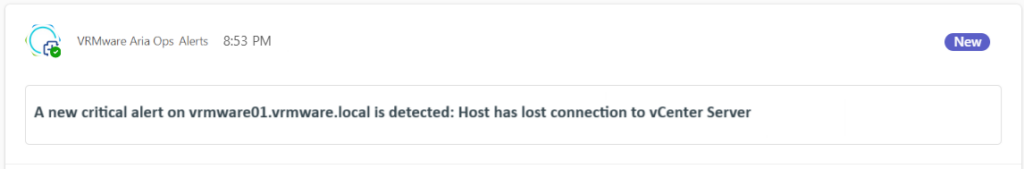
I hope this blog post will help you configure Aria Operations to send notifications to MS Teams. Please remember that MS Teams is not a monitoring tool. So be selective with the alerts you forward.
The payload code is based on the one that I found in this blog post from Brock Peterson.